INTELLIGENCE

messaging application. Yours.
The services offered by KRIPTERIA specialize exclusively in corporate protection systems, including defensive systems against large-scale threats.
We work with specific dynamics that combine corporate intelligence, cyber defense, solution design, process engineering, scheduling, online surveillance, social media and proximity monitoring skills.

… Before anything else, knowing what is going to happen today is the great secret of success
Information Consulting
Threat assessment, policy review and development, and planning of future actions
-
Consulting
Aimed at preventing future conflicts, through a critical analysis of data, situations and people. -
Assessment
Vulnerability assessment with 24/7 services.
System design
Development of specific plans, performance of evaluations and analysis of results
-
Competitiveness
We keep our companies competitive by constantly reviewing corporate security plans, with strict controls, both in the daily operations of the company and in its critical areas.
Operational Security
Solutions against corporate espionage, inside and outside the company
-
Security Protocols
Implementation of security protocols, sound internal information management practices, recruitment processes, efficient selection and risk reduction procedures, among others.
Cyber Defense
The security of our information, in recent years, has been compromised due to cyber espionage
-
Critical Information Management
We provide security to companies that handle critical information that must be preserved against attacks -
Reports
Intelligence reports, comprehensive security, design and application of countermeasures
KSE APP
With KSE your communications will always be secure
-
Security
Ofrecemos el borrado a distancia mediante la introducción de una clave personalizada así como la localización por GPS. -
Privacidad
Los mensajes se autodestruyen y sólo mientras son visualizados se almacenan de forma cifrada en la memoria del dispositivo.
What we do
We ease the
decission making process
Analysis
Know the vulnerabilities of the information assets and the threats that will attack our weaknesses.
THREAT DETECTION
Early detection of possible attacks on corporate security in our different areas.
INFORMATION
Report the risk detected and determine the process: accept it, transfer it, mitigate it or avoid it.
PROCESS APPLICATION
Prevent the filtration, misuse, or diversion of information to third parties according to the most beneficial procedure.
Professional ethics
Dynamism
Experience
Quality of service
Our clients

- Possibility of using your own server.
- Different layers of security.
- Integrated VPN.
- Screenshot notifications.
- Self-destruct messages on the device.
- End-to-end encryption even in group chats.
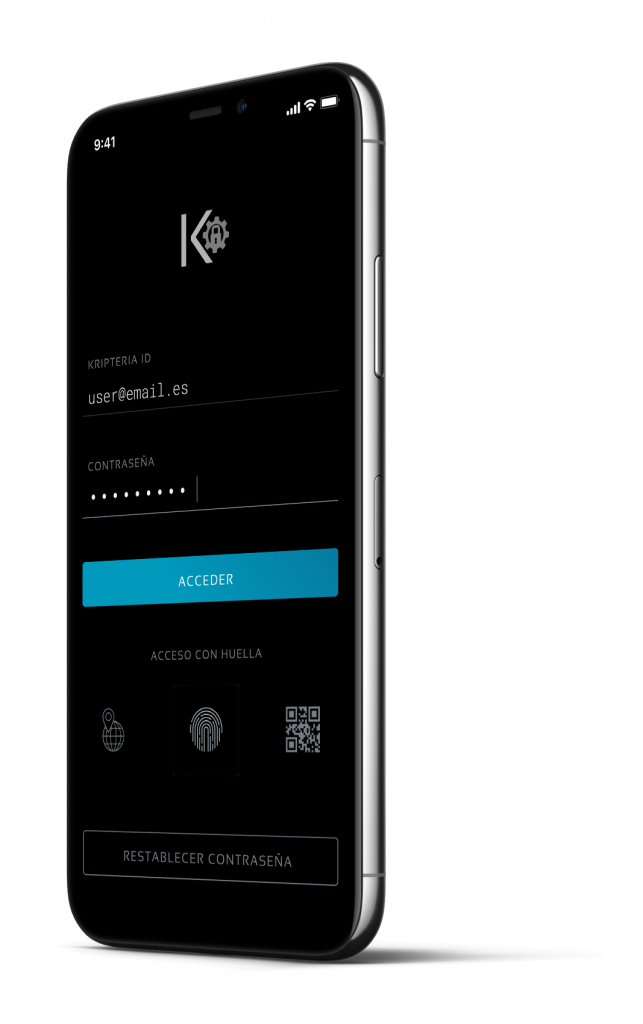
To meet our objective of providing timely and secure information, we provide our clients with an encrypted communication channel.
COMMUNICATION «1 TO 1»
IMMEDIATE INFORMATION ON
RISKS IN THE AREA
HIDDEN FOOTPRINT GPS
Hardware is easy to protect – lock it in a room, chain it to a desk, or buy a replacement. Information poses more of a problem. It can exist in more than one place; be transported to half the planet in seconds; and be stolen without your knowledge.
ISO CERTIFICACIONS